MultiPortal integrates with Proxmox to provide advanced networking capabilities, utilizing Software-Defined Networking (SDN) to create both external and internal virtual networks. This allows for flexible and scalable networking solutions within virtual environments, enabling seamless communication between virtual machines and external networks.
¶ Key Networking Features
MultiPortal's networking is based on two main types of virtual networks:
- VLAN (Virtual Local Area Network): Used for external networking.
- VXLAN (Virtual Extensible Local Area Network): Used for internal networking.
These networks are created within the Proxmox environment and managed through MultiPortal’s SDN functionality.
¶ Important Configuration Note
To ensure compatibility with VXLAN networks, switches and Proxmox environments should be configured with an MTU (Maximum Transmission Unit) of 9000. This ensures that the necessary requirements for VXLAN traffic are met, allowing for efficient network performance and reduced fragmentation.
¶ Reference Diagram
- PHYSICAL MAPPING - shows a sample representation of how your Proxmox Nodes are physically connected in the network.
- LOGICAL MAPPING - shows a sample of how the network is configured within Proxmox, including bridges, bonds, and VLANs. More details: https://pve.proxmox.com/wiki/Network_Configuration
- PROXMOX SDN - Defines network zones and virtual networks (VNets) within Proxmox’s Software-Defined Networking (SDN) setup. More details: https://pve.proxmox.com/wiki/Software-Defined_Network
- MULTIPORTAL NETWORKING - defines how MultiPortal utilizes Proxmox SDN to create Internal and External networks
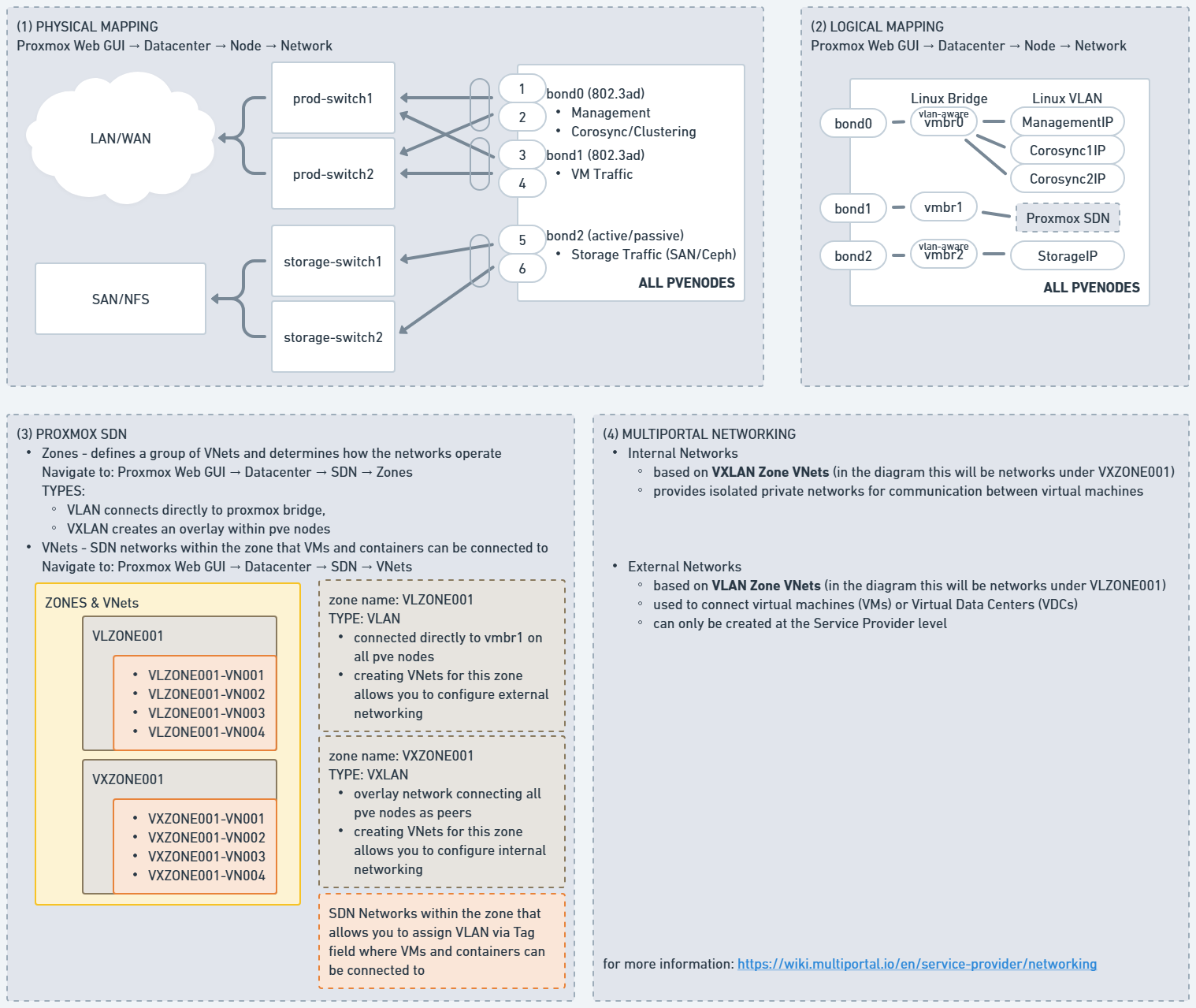
¶ External Networking
External Networks in MultiPortal are based on VLAN VNets. These networks are used to connect virtual machines (VMs) or Virtual Data Centers (VDCs) within MultiPortal to VLANs that exist outside of the MultiPortal environment.
External Networks can only be created at the Service Provider level.
¶ Key Features:
- VLAN Integration: External networks allow VMs to be directly connected to external VLANs from the broader network.
- WAN Connectivity: This setup is commonly used to connect virtual routers or other networking devices to WAN (Wide Area Network) VLANs.
- External Access: VMs or entire VDCs can be connected to external networks, enabling access to resources and services outside of the MultiPortal environment.
¶ Use Cases:
- Connecting a virtual router to a WAN VLAN for internet access.
- Providing access for VMs to services on an external network (e.g., connecting a web server in a VDC to the internet).
¶ Important Notes:
¶ Bridges
- When creating an External network, a bridge must be selected. The External network's intended VLAN must be accessible via this bridge
- A bridge is can be thought of as a virtual switch, and allows a Proxmox node to connect to the physical network. By default, all nodes deploy with a bridge called vmbr0, however others can be created if there is a need to connect Proxmox to multiple physical networks
- To ensure an External network operates consistently correctly across the datacenter, it is recommended that all bridges exist on all nodes with consistent names and connected to the same physical network. This is especially important when using HA as VMs may be moved between nodes automatically
¶ How to Configure Proxmox SDN for External Networking:
¶ 1. Create the VLAN Zone
- Go to Datacenter > SDN > Zones
- Click "Add", choose VLAN and fill the details below
ID: (e.g., L001)
Bridge: Choose an existing Linux bridge (e.g., vmbr0)
MTU: Specify MTU (e.g., 9000)
Nodes: default (All)
IPAM: default (pve) - Click "Add" to save.
¶ 2. Create the VLAN VNet
- Go to Datacenter > SDN > VNets
- Click "Create" and set:
ID: (e.g., L0010068)
Alias: Human-friendly name or an alternative identifier for the VNet. (e.g., VLAN68)
Zone: Select the VLAN Zone created earlier (e.g., L001).
Tag: Set the VLAN ID (e.g., 68) - Click "Create" to save.
¶ 3. Apply SDN Changes
- Go to Datacenter > SDN
- Click "Apply" to commit the changes
This will push the configuration to all nodes in the cluster. - You may now use the newly created VNet in MultiPortal
¶ Internal Networking
Internal Networks in MultiPortal are based on VXLAN VNets, providing isolated private networks for communication between virtual machines within MultiPortal.
Internal Networks can be created at the Service Provider level and allocated to tenants/vDCs, or tenants can create their own and allocate them to their vDCs
¶ Key Features:
- Isolated Private Network: Internal networks create isolated, internal LAN networks for VMs to communicate securely and privately.
- VXLAN Virtualization: VXLAN VNets allow for scalable, flexible internal networking by extending Layer 2 networks over a Layer 3 infrastructure, making them ideal for large-scale virtual environments.
- Internal Communication: This network type is used when VMs need to communicate with each other within a private virtual environment, without exposing services to external networks.
¶ Use Cases:
- Setting up a private internal network for VMs within the same VDC to communicate securely.
- Creating an internal LAN for a set of VMs to interact without external network access.
¶ How to Configure Proxmox SDN for Internal Networking:
¶ 1. Create the VXLAN Zone
- Go to Datacenter > SDN > Zones
- Click "Add", choose VXLAN and fill the details below
ID: (e.g., X001)
Peer Address List: Specify the IP addresses of your nodes separated by comma (e.g., 192.168.1.1, 192.168.1.2, 192.168.1.3)
MTU: Specify MTU (e.g., 9000)
Nodes: default (All)
IPAM: default (pve) - Click "Add" to save.
¶ 2. Create the VXLAN VNet
- Go to Datacenter > SDN > VNets
- Click "Create" and set:
ID: (e.g., X0010100)
Alias: Human-friendly name or an alternative identifier for the VNet. (e.g., VXLAN100)
Zone: Select the VLAN Zone created earlier (e.g., X001).
Tag: Set the VXLAN TAG (e.g., 100) - Click "Create" to save.
¶ 3. Apply SDN Changes
- Go to Datacenter > SDN
- Click "Apply" to commit the changes
This will push the configuration to all nodes in the cluster. - You may now use the newly created VNet in MultiPortal
¶ Conclusion
MultiPortal's networking architecture leverages the SDN capabilities of Proxmox to create both VLAN-based External Networks and VXLAN-based Internal Networks. The external networks allow for connection to outside VLANs and external services, while internal networks provide isolated private communication between VMs. Proper configuration of MTU 9000 is essential for ensuring that VXLAN traffic performs efficiently. This flexible and scalable approach to networking makes MultiPortal suitable for complex virtualized environments.