¶ Console Server
The Console Server is an internal Node.js application that runs alongside MultiPortal, creating a secure WebSocket connect between your MultiPortal to your Proxmox servers. It automatically starts when MultiPortal is installed and is monitored every minute to ensure it's running smoothly.
¶ System Requirements
When setting up the Proxmox integration, ensure that the username and password provided have the necessary permissions to access the Proxmox console. Without proper access, MultiPortal will be unable to establish console connections to your virtual machines. To set up your user you can read Creating A Proxmox API User.
¶ SSL Requirements
Your MultiPortal instance must have a valid SSL certificate to establish a secure connection between itself and your Proxmox instances.
¶ Monitoring the Console Control Panel
The Console Control Panel is now fully integrated into the Web GUI, simplifying monitoring and management tasks. PM2 continues to ensure the service's reliability in the background, but manual command-line interaction is no longer required for routine operations.
¶ Accessing the Console Control Panel
- Log in to the Web GUI using your administrator credentials.
- Navigate to the Console Control Panel section under the Settings menu.
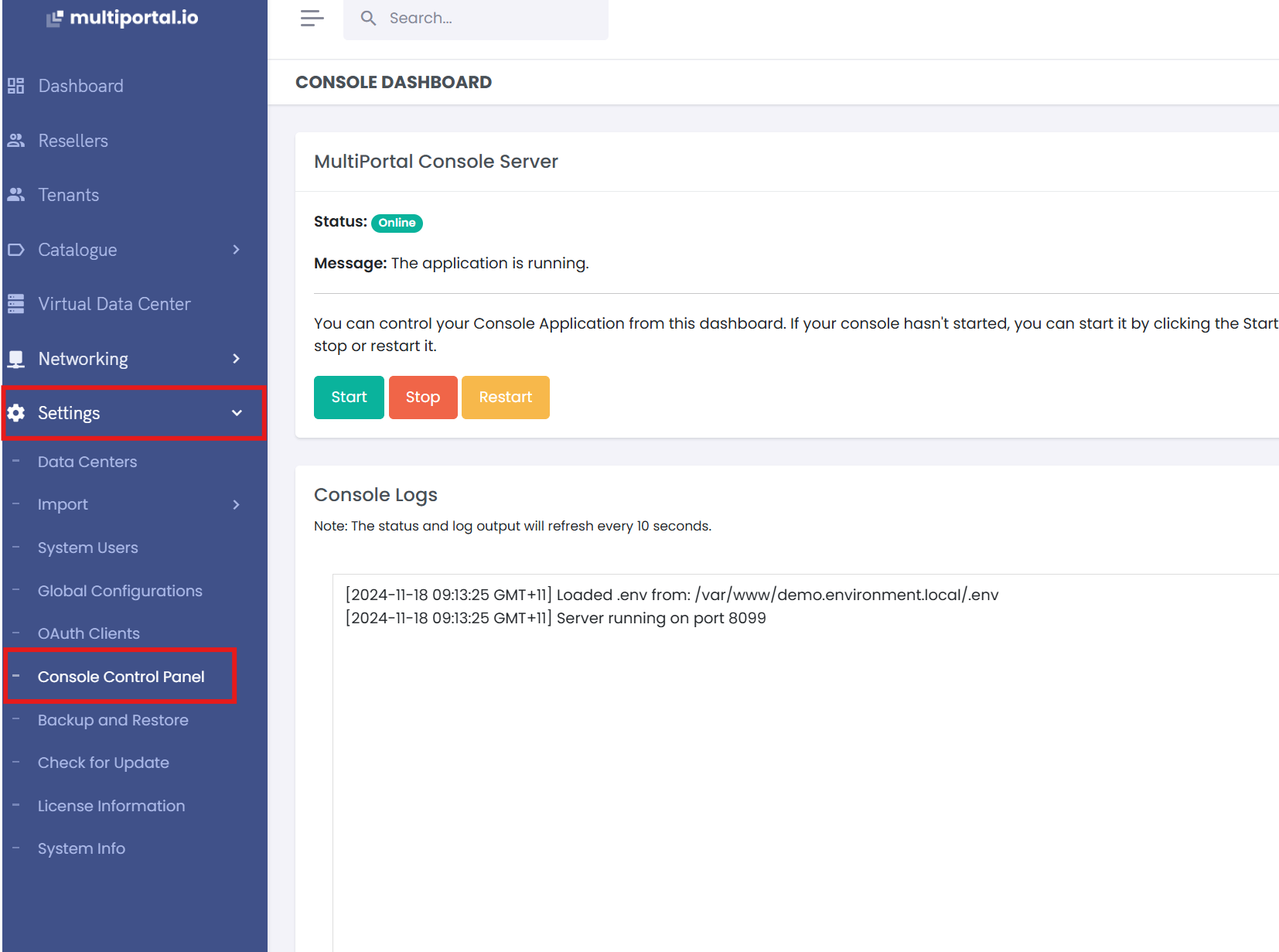
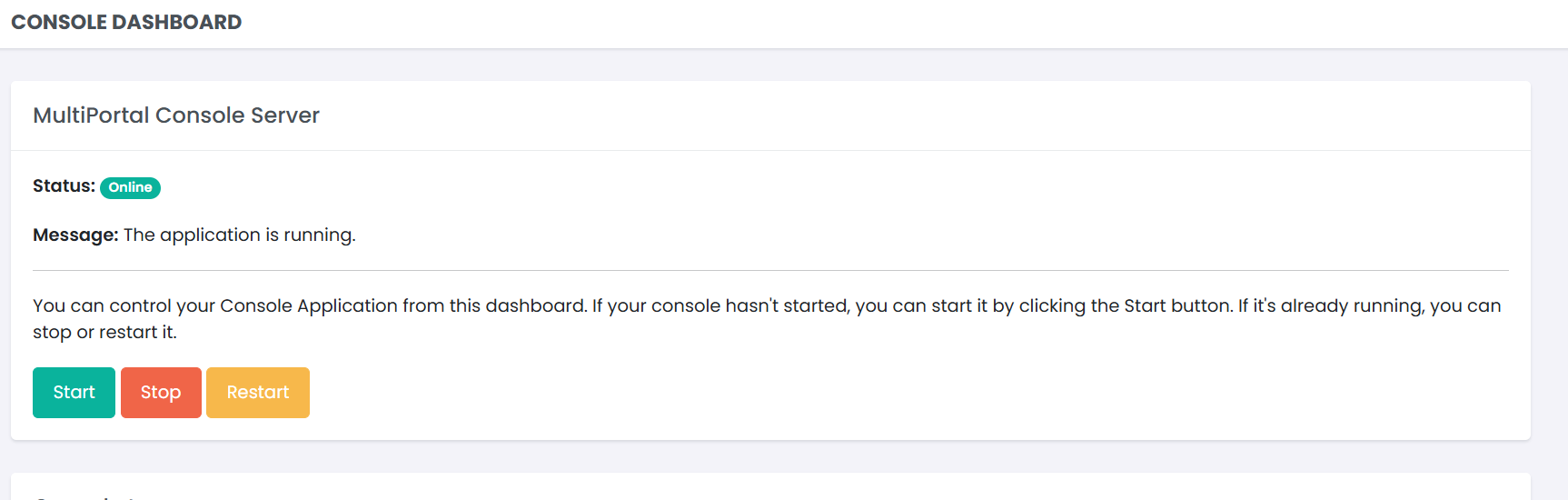
¶ Features Available in the Web GUI:
- Status Overview: View the current state of the Console Control Panel (e.g., running, stopped).
- Start, Restart, or Stop: Manage the service directly from the Web GUI with easy-to-use controls.
- Logs and Troubleshooting: Access and review real-time logs for troubleshooting.
¶ Advanced Manual Checks (Optional)
For advanced users or troubleshooting purposes, the PM2 tool is still available on the server. You can manually verify the service status or perform actions using commands like:
-
View the PM2 process list:
sudo -u www-data pm2 list -
Check logs:
sudo -u www-data pm2 logs
However, these steps are typically unnecessary, as the Web GUI now centralizes all key functionalities.
¶ Logging
After version 0.6.1, when the system restarts the PM2 service, a new log file called console_output.log is created. This file is crucial for debugging and troubleshooting any issues related to the Console Server.
The log file can be found in:
/var/www/FQDN/logs/console_output.log
¶ Troubleshooting Console Server Issues in MultiPortal
Follow the video below for a step-by-step walkthrough of resolving common console server issues, or read on for detailed instructions.
¶ Common Issues and Solutions
¶ 1. Failed to Retrieve PM2 Status
- Issue: PM2, which runs the console server, fails to retrieve the status.
- Solution:
- Click the Start button in the Console Control Panel.
- If successful, the application will indicate that it is running.
- Attempt to connect to your virtual machine (VM) via the console.
¶ 2. Missing or Invalid API Token
- Issue: The console server requires an API token to create a secure tunnel between MultiPortal and your Proxmox environment. A missing or invalid token can prevent connection.
- Solution:
- Navigate to your server and run:
./yii generate-api-key- If a token already exists, you'll receive a message indicating so.
- To regenerate a token, use:
./yii generate-api-key/replace
- Restart the console server from the Console Control Panel to apply the new token.
- Navigate to your server and run:
¶ 3. Host File Configuration
If you're using a custom DNS name that is not publicly accessible, your MultiPortal server might encounter issues when attempting to establish a secure connection for the console server. These issues can manifest as latency or connection failures, as the server struggles to resolve its own domain name.
To ensure your MultiPortal Console communicates correctly with itself, update the host file to map the MultiPortal domain to the localhost.
- Issue: MultiPortal fails to connect to itself efficiently, causing latency or connection errors.
- Solution:
- Open the host file on your MultiPortal server:
sudo nano /etc/hosts - Add an entry mapping your MultiPortal domain to
127.0.0.1:127.0.0.1 multiportal.example.com - Save and close the editor (
Ctrl+O,Enter,Ctrl+X). - Restart the relevant service to apply the changes (if needed):
sudo systemctl restart caddy
- Open the host file on your MultiPortal server:
By making this change, the MultiPortal server will correctly route requests to itself, resolving potential connection issues. You can verify the resolution by testing the console connection functionality.
¶ 4. Incorrect Data Center Credentials
-
Issue: In older MultiPortal versions, data center credentials were not validated during setup. This could result in connection failures or errors after the production release.
-
Solution:
- Navigate to the Data Center Settings in MultiPortal.
- Verify and update the Username and Password fields as required.
- Click the Test button to validate the API connection.
- If the credentials are incorrect, an error message will appear.
- Correct the credentials and save your changes.
-
Troubleshooting:
- If the test still fails, ensure:
- The data center is accessible from the MultiPortal server.
- The API endpoint is correctly configured.
- The credentials have the necessary permissions.
- Contact MultiPortal Support for further assistance.
- If the test still fails, ensure:
¶ 5. Error in WebSocket connection: unable to verify the first certificate
-
Issue: When using Custom SSL, connecting to virtual machines' console doesn't work and shows 'Connecting.'
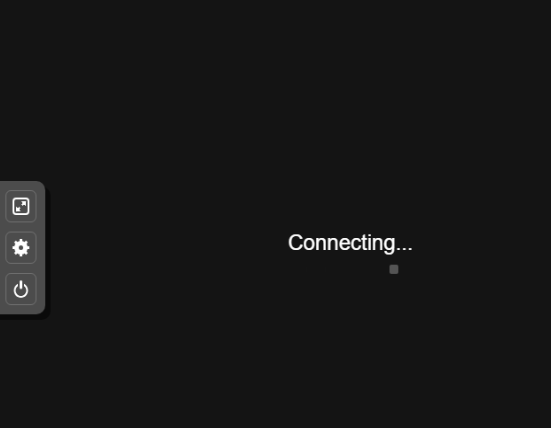
When viewing the Console logs, you will also see the following error:
Error in WebSocket connection: unable to verify the first certificate -
Solution:
- Verify that you are using a full chain certificate provided by your vendor.
- A full chain certificate includes all necessary intermediate certificates to establish trust.
- You can use the following command to check:
Ensure that the output lists all certificates in the chain, up to the root certificate.openssl s_client -connect your-domain:443 -showcerts
- If you update the certificate, restart Caddy to apply changes:
systemctl restart caddy
- Verify that you are using a full chain certificate provided by your vendor.
¶ Need Help?
If you have completed the steps above and are still encountering issues, please reach out to MultiPortal Support for assistance.